What is Phishing?
Phishing is an email attack attempting to trick you into either opening an attachment that contains a virus, clicking a web link that contains a virus, or visiting a website that creatively asks for personal information. As a general rule of thumb, don’t click links!
A Changing Approach to Phishing Attacks
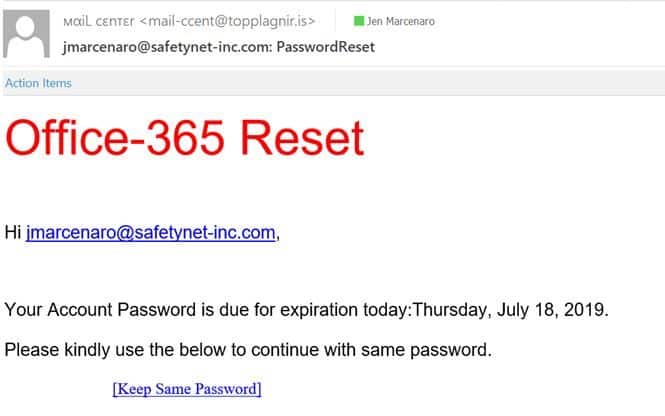
Compromised accounts result from clicking on a link and voluntarily entering your confidential information or answering questions that are intended to gather details a hacker can use to figure out your login info. Trust us, don’t click links unless you’re 100% certain they’re legit.
Cybercriminals are becoming increasingly tricky and successful at getting past spam filters and virus detection systems with phishing attacks. In highly targeted attacks, the emails appear to originate from somebody you know.
If you receive suspicious emails, whether they’re from someone you know or don’t, DO NOT CLICK LINKS OR OPEN ATTACHMENTS. Instead, do the following:
- If you don’t know the sender and it’s clearly something you don’t need, delete it and move on.
- If you don’t know the sender but think it may be legitimate, contact the organization that supposedly sent the message to verify the validity of the message.
- If you know the sender, but something about the email looks odd, contact them to confirm they intentionally sent it to you. Often after people get a virus or have their account compromised, messages are sent from their accounts by the perpetrator. It’s best to contact the “sender” verbally because if their account is compromised, the perpetrator may be the one reading or responding to your message.
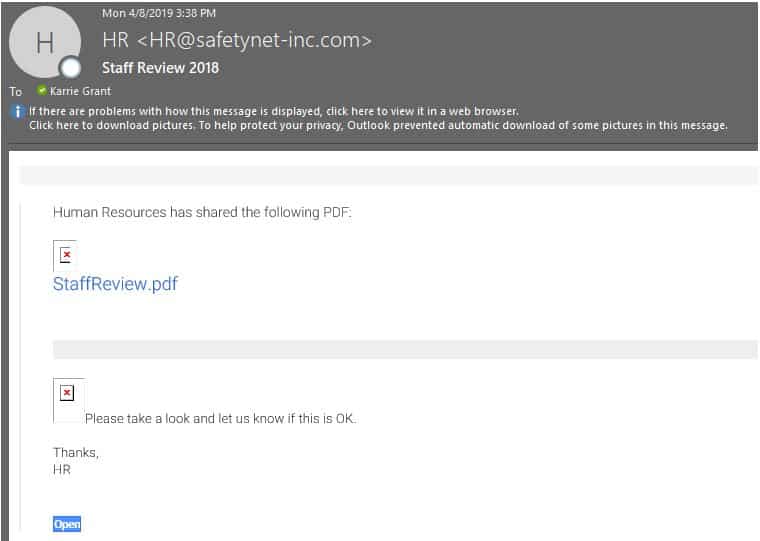
There’s not an HR@safetynet email address in our organization. We also have a very small HR department, so it’s unlikely they would sign an email with “HR.”
Phishing Links
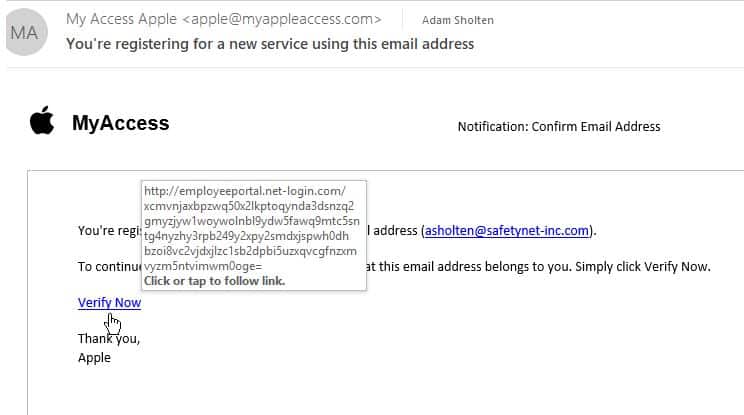
To identify a bad link, hover over it with your mouse – don’t click the link. The real web address will show up. It’s generally obvious that something isn’t right.
- The domain name may be different than that of the sender, or it isn’t one associated with a legitimate company.
- Instead of .com or .org at the end of a URL, you might see .ro, .cn, or .ru indicating a site is based in Romania, China, or Russia – countries known to harbor cyber criminals. Those are just some examples, as hackers can live and work anywhere.
- A common company name may be used, but there is a misspelling, ex. microsotf.com.
If you suspect you clicked a bad link, or if the sending party can’t verify that a message is legitimate, contact your IT support immediately.



