Category Archives: Security
Microsoft Security Certificate Vulnerability
We are aware of and actively monitoring a recently identified security certificate vulnerability affecting Windows [...]
Jan
Cyber Security Information and Trends
This collaborative piece on cyber security was skillfully written and originally published by Oneupweb – [...]
Dec
Internet of Things (IoT) – What you Need to Know
The IoT is the system of devices that connect to the internet and to each [...]
Dec
Nastiest Malware of 2019 according to Webroot
Originally published by Webroot on 10/29/19 (https://community.webroot.com/news-announcements-3/nastiest-malware-2019-340824) As National Cybersecurity Awareness month comes to an [...]
Oct
Your Online Safety: Own IT. Secure IT. Protect IT.
October is National Cybersecurity Awareness Month (NCSAM). This year’s theme, as determined by the National [...]
Oct
Business Continuity Plan: Can Your Company Survive a Disaster?
No business owner expects their company to face a debilitating crisis. Most successful businesses are [...]
Aug
Phishing Attacks: The #1 Reason We Say “Don’t Click Links”
What is Phishing? Phishing is an email attack attempting to trick you into either opening [...]
Jul
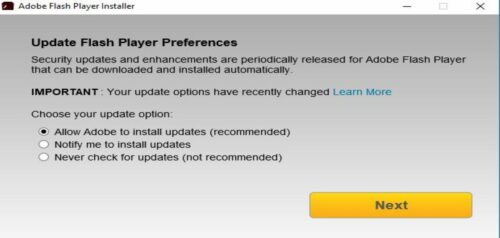
Updates: To Install or Not to Install?
It’s hard to know when an unexpected pop-up on your screen is legitimate. What do [...]
Jul
Can my Social Security Number be Suspended?
Recently, our friends at KnowBe4 warned us of robocall scams saying your Social Security Number [...]
Apr
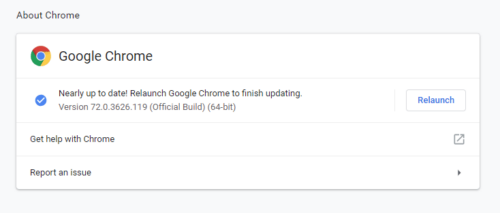
Vulnerability Exposed – Urgent Update of Chrome Browser Required
A security vulnerability has been identified in the Google Chrome application. To put it simply, hackers [...]
Mar